Creating an Active-Active VPN Tunnel with BGP in Azure
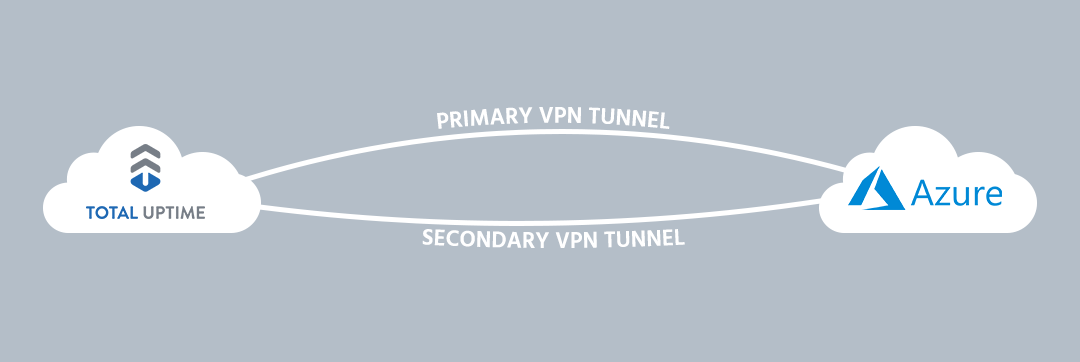
In this article we will outline the steps required to create an active-active VPN tunnel with BGP dynamic routing between Microsoft Azure and the Total Uptime Cloud Platform.
By default, Total Uptime requires your devices (servers) to have internet-routable IPv4 or IPv6 addresses so we can direct traffic to them. By creating VPN tunnels between the Total Uptime platform and Microsoft Azure, you can avoid the requirement for public IP space and securely route traffic to your cloud devices with a very high degree of availability.
Regardless of whether you use a VPN or not, Total Uptime already has direct network connectivity to Microsoft Azure with private peering to ensure high performance connectivity. Adding a VPN simply encrypts that traffic and allows you to use RFC1918 space.
Prerequisites
To begin you will require a few things.
- A virtual network subnet approved by Total Uptime: ____________
- An ASN approved by Total Uptime for use on the Azure side of the BGP connection: _________
- The Total Uptime ASN, which is: 53334
- The Total Uptime VPN gateway IP addresses: ____________ and ____________
- The Total Uptime BGP peer IP addresses: ____________ and ____________
- A pre-shared key for the VPN (you can create this)
STEP 1: Create a Virtual Network
The Virtual network is the private, non-routable subnet that will be used in Azure. IP addresses will be assigned from this range to your devices which will become accessible via the Total Uptime cloud.
If you already have infrastructure at Azure, you most likely already have this network. In this case, please confirm with Total Uptime that the subnet you are already using is available for linking to the Total Uptime cloud. If you are new to Azure, please request an unused subnet from Total Uptime for use in Azure. This will make things much simpler and cleaner.
To add the virtual network:
- Log in to your Azure subscription
- Click on ‘All Services’ in the navigation pane
- Search for ‘Virtual Networks,’ and select the ‘Virtual Networks’ service.
- Click the ‘+Add’ button.
- Name the network, then specify its address space, resource group, location, subnet name, subnet address range.
- Click the ‘Create’ button.
Once deployed you will receive an on-screen notification. In that notification click the ‘Go to resource’ button to open the new virtual network that was just created. We now need to create a Gateway Subnet. This subnet is a smaller portion of the larger subnet. We recommend nothing smaller than a /28. From this range IP addresses will be assigned automatically by Azure for the local BGP peers.
- Under ‘Settings’ click on ‘Subnets.’
- Click on the ‘+Gateway Subnet’ button.
The name will be ‘GatewaySubnet’ and cannot be changed. Specify the address range and click the ‘OK’ button.
STEP 2: Create a Virtual Network Gateway
We now need to create virtual network gateways. These are essentially small VPN VMs that will receive a public IP address for Total Uptime to build a tunnel to. They will also map/allow the virtual network from step 1 for announcement via BGP.
- Click ‘All Services’ in the navigation pane, search for ‘Virtual Network Gateways,’ and click on the service.
- Click the ‘+Add’ button.
- Name the virtual network gateway. (e.g. AZ-to-TUT-VPN)
- Select ‘VPN’ as the gateway type.
- Select ‘Route-based’ as the VPN type.
- Select ‘VpnGw1’ or higher for the SKU.
- Put a check mark in the ‘Enable active-active mode’ box.
- Select the virtual network you just created.
- Unless you already have a public IP address to assign to this, select ‘Create new’ for the public IP address and give it a name. Basic SKU and dynamic assignment will be selected by default.
- Select ‘Create new’ for the second IP address and give it a name. Basic SKU and dynamic assignment will be selected by default.
- Put a check mark in the ‘Configure BGP ASN’ box and specify the ASN assigned to you by Total Uptime.
- Specify your subscription.
- Specify the location.
- Click the ‘Create’ button.
STEP 3: Create Local Network Gateways
You will create two local network gateways in this step. These will represent the public IP addresses of the Total Uptime routers that the VPN tunnels will be built to.
- Click ‘All Services’ in the navigation pane, search for ‘Local Network Gateways,’ and click on the service.
- Click the ‘+Add’ button.
- Name the connection (e.g. TUT-to-AZ-VPN1) and specify the IP address of the Total Uptime routers assigned.
- Specify the BGP peer IP in the ‘Address Space’ text box, appending a /32 to it (this section is technically the subnets on the Total Uptime side, but because we have a BGP connection, we’ll announce these subnets to you instead, and since Azure doesn’t allow this to be blank, we enter the same Ip as the BGP peer IP address.)
- Put a check mark in the ‘Configure BGP settings’ box, then specify our ASN and BGP peer IP address.
- Select the resource group to which you’d like this gateway attached.
- Specify the location.
- Click the ‘Create’ button.
- Run through the steps again for the second connection.
STEP 4: Create the VPN Connections
Now we build the two tunnel configurations between Azure and Total Uptime. We will be creating an IPsec/IKE policy and the two connections using the Azure cloud shell.
Open the Azure cloud shell by clicking on the ‘>_’ button in the top toolbar as depicted below:
![]()
Declare your variables for use in the subsequent commands. Edit to match your setup.
$RG1 = "<YourResourceGroupName>"
$Location1 = "<YourLocation>"
$GWName1 = "<YourVirtualNetworkGatewayName>"
$LNGName1 = "<YourFirstLocalNetworkGatewayName>"
$LNGName2 = "<YourSecondLocalNetworkGatewayName>"
$Connection1 = "<YourFirstConnectionName>"
$Connection2 = "<YourSecondConnectionName>"
Now run the following to create the IPsec/IKE policy.
$ipsecpolicy1 = New-AzureRmIpsecPolicy -IkeEncryption AES256 -IkeIntegrity SHA256 -DhGroup DHGroup14 -IpsecEncryption AES256 -IpsecIntegrity SHA256 -PfsGroup None -SALifeTimeSeconds 14400 -SADataSizeKilobytes 102400000
Next you will create the site-to-site VPN connections. Edit to match your setup.
$vnet1gw = Get-AzureRmVirtualNetworkGateway -Name $GWName1 -ResourceGroupName $RG1
$lng1 = Get-AzureRmLocalNetworkGateway -Name $LNGName1 -ResourceGroupName $RG1
$lng2 = Get-AzureRmLocalNetworkGateway -Name $LNGName2 -ResourceGroupName $RG1
New-AzureRmVirtualNetworkGatewayConnection -Name $Connection1 -ResourceGroupName $RG1 -VirtualNetworkGateway1 $vnet1gw -LocalNetworkGateway2 $lng1 -Location $Location1 -ConnectionType IPsec -IpsecPolicies $ipsecpolicy1 -SharedKey ‘<YourSharedKey>’ -EnableBgp $True
New-AzureRmVirtualNetworkGatewayConnection -Name $Connection2 -ResourceGroupName $RG1 -VirtualNetworkGateway1 $vnet1gw -LocalNetworkGateway2 $lng2 -Location $Location1 -ConnectionType IPsec -IpsecPolicies $ipsecpolicy1 -SharedKey ‘<YourSharedKey>’ -EnableBgp $True
Click ‘All Services’ in the navigation pane, search for ‘Connections,’ and click on the service. You should see the two new connections you just created.
If you click on a connection, the blade that opens provides an option to download the configuration script for several devices.

We require the “Generic Samples” configuration script in order to complete the Total Uptime side. Please note you may get an error when trying to download the script when BGP is enabled on the connection. In that case you will need to disable BGP in the connection’s configuration first, and then enable it after downloading the script.
STEP 5: Deliverables to Total Uptime
Please provide the following items to your contact at Total Uptime:
- The sample config files you just downloaded (the pre-shared key is inside them).
- The BGP peer IP addresses from the virtual network gateway that Azure assigned out of the smaller subnet.
- A private IP address for a virtual machine at Azure that is within the virtual network subnet that will respond to ICMP echo/ping so we can test connectivity after building the configuration on the Total Uptime side.
Information about whether or not you currently have any virtual machines in this environment that are behind Total Uptime already (most likely via a public IP).
If you have existing virtual machines behind the WAF or Load Balancer, we will need to turn up BGP during a mutually agreeable maintenance window since the IP space that the load balancers use will shift to the tunnels. If you do not, then we can turn up BGP immediately and provide test parameters.