VPN Load Balancing and Failover with two ISPs
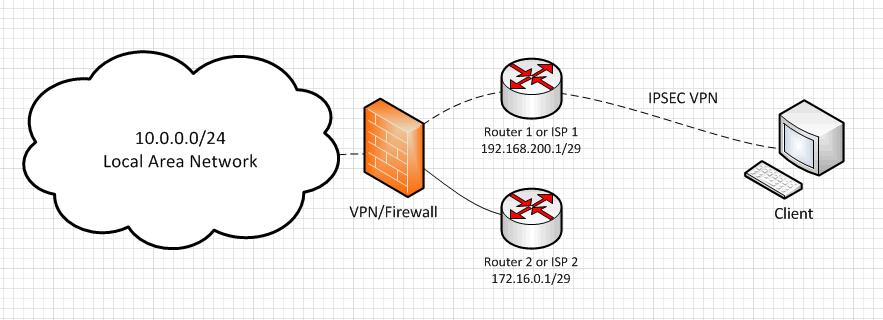
A common SSL or IPSEC VPN configuration scenario is one like we’ve shown in the (simplistic) diagram below. A corporate office has two incoming ISP connections, each with their own range of IP addresses. Clients or sites have VPN connections to the corporate office to access back-office devices in the LAN. The problem arises when the primary router or ISP goes offline. VPN tunnels that are configured using a DNS name don’t fail over until DNS is updated, which is something our DNS Failover solution can nicely solve. But what about connections that rely on static IP addresses. I know Cisco ASA point-to-point VPNs require a fixed IP address, which is not uncommon amongst VPN hardware vendors. So what do you do in that case?
Total Uptime Cloud Load Balancing can help in this situation too. We can step into the middle, between the client and your public facing Internet connections in order to provide something almost equal to a VPN cloud. The image below explains how this works pretty quickly. Because you’re given a static IP in our cloud, all VPN clients and tunnels use this as the VPN end-point. When we receive the traffic we simply proxy it over to the currently active IP address associated with your router or firewall, or if desired and capable, we evenly distribute incoming connections between the two ISPs. When the IP fails to respond based on the monitoring you specify, we automatically stop sending traffic to that link. Of course, this results in a disconnect for the clients traversing that VPN tunnel, but the tunnel is quickly reestablished within a matter of seconds.
Consider another scenario – a typical configuration where a larger organization has two offices. Each office has their own firewall and VPN appliance for clients and other sites to connect. Additionally, each office is connected to the other by a private line. In this scenario, Total Uptime can also distribute VPN client connections to each office’s VPN appliance so when one ISP link goes down, VPN tunnels will reestablish through the remaining office. Because the two offices are interconnected via a private line, the clients can still connect to the LAN.
Of course, there really is no limitation to the different configuration possibilities. We can route traffic to 1, 2, 3 or a dozen different servers or devices. We can route any TCP or UDP port you’ll ever need and have successfully worked with almost any type of connection from DSL and Cable to T1 lines and more. Plus, it doesn’t matter where the connections are located around the world. We probably have a cloud node somewhere nearby. These are merely ideas that we’ve helped clients configure time and again. If you have a unique situation that could use some redundancy and uptime improvement, reach out to us! We’re happy to discuss all of the possibilities to determine if there is a way we can help your organization.
 What is an Application Delivery Network?
What is an Application Delivery Network?  Global Server Load Balancing (GSLB)
Global Server Load Balancing (GSLB)  Measuring Failure
Measuring Failure