Our Positive Security Model Delivers Zero Day Protection
At the edge of the internet
Next-generation security requires much more than simple packet-level inspection.
The application security technology of Web Application and API Protection (WAAP) is based on a positive security model that ensures correct application behavior. The model is based on HTTP industry standards and best coding practices for APIs, HTML and JavaScript. Application behavior deviating from the positive security model is treated as potentially malicious and is blocked by the WAAP.
Through its understanding of good application behavior, the positive security model does not require attack signatures or pattern matching techniques to detect and block attacks. It is the only proven approach delivering zero day protection against unpublished exploits. The positive security model:
- Models application behavior
- Verifies best practices
- Ensures RFC compliance
- Enforces security in real-time
- Is not signature-based
Deep Content Inspection
Next-generation security requires much more than simple packet-level inspection. Complete application security requires deep stream inspection technology that reconstructs all bi-directional communications for each user session. Once reconstructed, it inspects all content to ensure correct application behavior, and the validity of user and machine inputs.
Deep stream inspection technology is based on multiple core technologies, including:
- Bi-directional analysis of all application traffic
- Complete header and payload inspection
- Full application parsing
- Semantic extraction of relevant application objects
- Traffic sessionization
Adaptive Learning Engine
In addition to delivering out-of-the-box protection against all Web-based threats, Web Application and API Protection provides the ability to tailor security policies for any application, including those using client-side JavaScript. The adaptive learning engine can automatically learn the behavior of an application and generate human-readable policy recommendations. The security manager can then selectively apply recommendations to strengthen a security policy and to enable permissible application behavior.
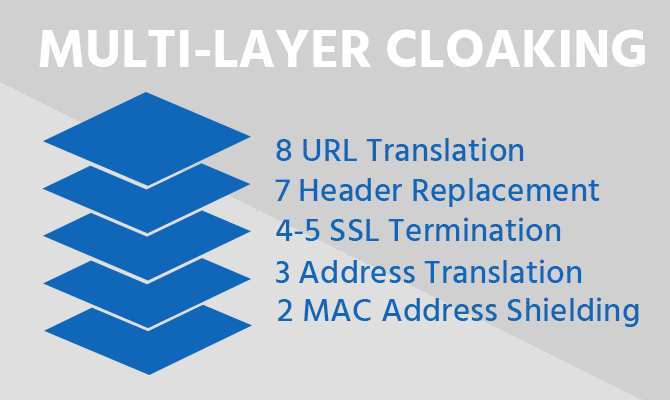
Multi-layer Cloaking
Total Uptime Web Application and API Protection incorporates multi-layer cloaking technology to mitigate a hacker’s ability to conduct reconnaissance on a target API or website. It hides sensitive information about an application environment (e.g., application server, database technology, server operating system, internal domain naming, etc.) making it much more difficult for an attacker to devise an effective attack strategy and exploit known vulnerabilities. By cloaking sensitive or revealing information at multiple communication layers, hackers are denied valuable intelligence about an application infrastructure, thus greatly reducing the risk of attack.