Block harmful traffic from the internet before it gets near your devices
Shield your network from the ever growing number of DDoS and application-layer attacks.
Our Global WAAP Platform
We operate one of the largest performance-based, datacenter independent Anycast WAAP/WAF networks in the world with native IPv6 support.
Our WAAP platform is globally distributed utilizing hundreds of different network providers. What does this mean for our customers? It's simple: Better performance, redundancy, scalability, capacity. We route traffic for small businesses on up to some of the world's largest corporations.
More about our network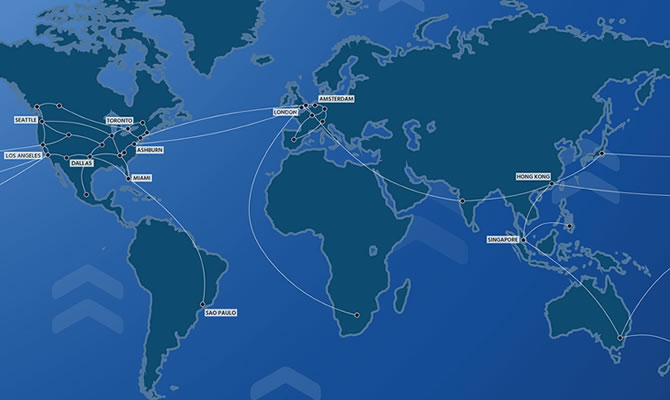
OWASP Attack Prevention
The WAAP defends against 15 classes of web application vulnerabilities.
There are 15 classes of application vulnerabilities, and Total Uptime protects against every one of them. From Buffer Overflow Exploits to Cookie/Session Poisoning to SQL Injection, we've got you covered. Without complete 15-out-of-15-protection, applications and APIs are exposed to unnecessary risks. All classes are completely customizable to suit every unique requirement.
More about Exploit Protection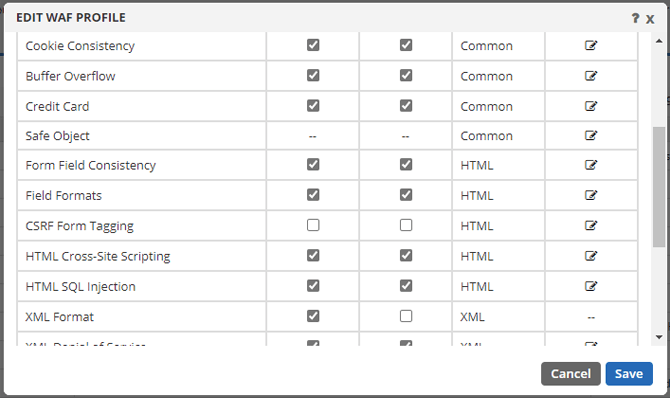
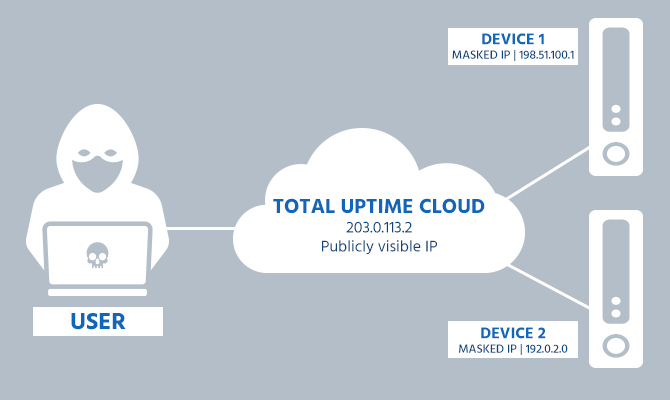
Origin Stealth
Only the Total Uptime IP is visible on the internet. Your device IP addresses are hidden behind our WAAP network.
Zero Day Protection
Deep content inspection and multi-layer cloaking
The application security technology of the WAAP is based on a positive security model that ensures correct application behavior. The model is based on HTTP industry standards and best coding practices for HTML and JavaScript. Application behavior deviating from the positive security model is treated as potentially malicious and is blocked by the Total Uptime's Web Application and API Protection platform.
More about the positive security model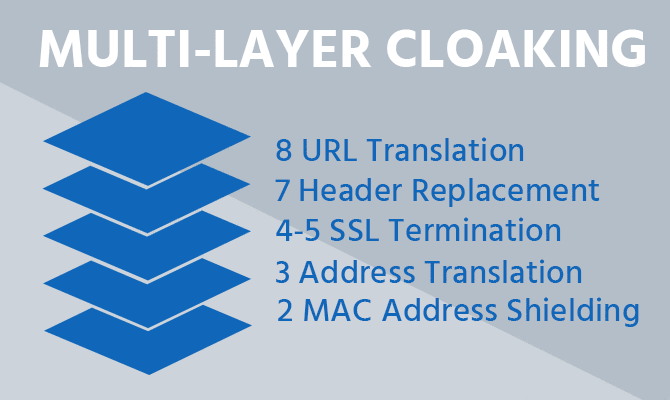
Prevent Information Disclosure
WAAP delivers PCI-DSS compliance
Total Uptime's WAAP protects sensitive application content which, if leaked, could result in fraud and identity theft. The business object protection modules provided in the WAAP offer predefined object protection (i.e., U.S. Social Security numbers [SSNs] or credit card numbers) and the capability to protect any administratively-defined data objects.
More about information disclosure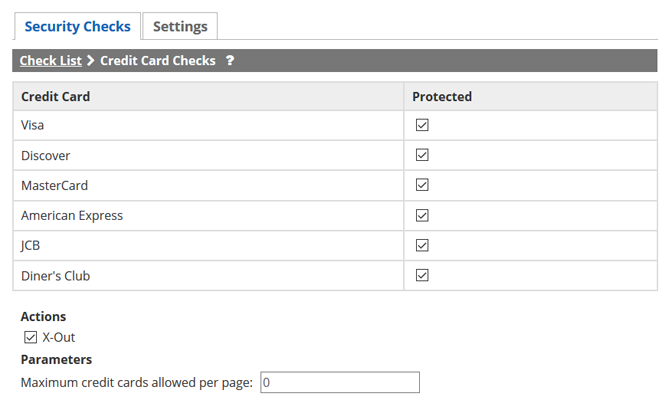
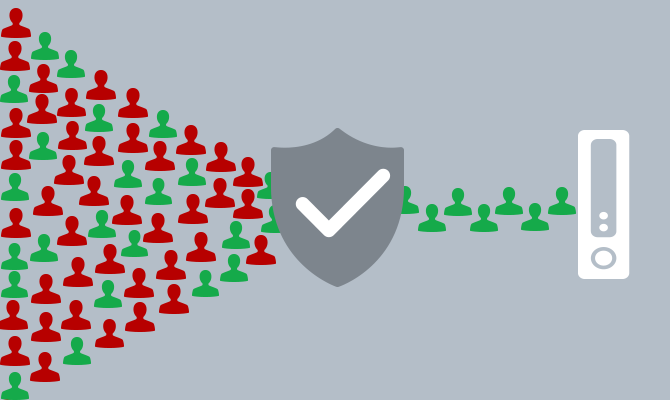
Denial of Service (DoS) Defense
Stop malicious distributed denial-of-service (DDoS) attacks at the edge of the internet well before they reach your data center or devices, on-prem or in the cloud.
- Volumetric attacks
- SYN floods
- Teardrop attacks
- Fraggle attacks
- Zombie connections
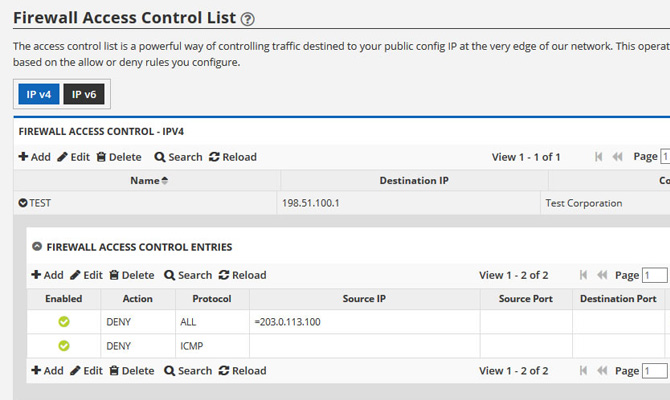
Country Blocking and Access Control Lists
Easily block entire countries or even single IP addresses. Create custom rules based on port, protocol, IP range and more with our powerful and flexible Layer 3 ACL.
Reporting & Analytics
View malicious traffic in real-time with intuitive graphs and detailed logs that provide critical information exactly when you need it.
Monitor account utilization data by date and time and make decisions quickly and easily. Web Application and API Protection is only good if you can get the details!
Role-Based Security
Create multiple user accounts and assign them to any number of different roles to completely control access.
Designed for Developers too
Total Uptime's REST API allows you to skip the UI, build your own, or simply automate and fit our features into your workflow. Our API offers in-depth documentation and how-to articles. Almost all of the data and functionality within our UI is accessible through the API, so the possibilities are endless.

Support on your terms - 24xForever
Supported by the same team that built the platform
We're always here to help when needed. Phone, email, chat, whatever your preference, you'll be helped by a knowledgeable team that actually cares.
We're even happy to help you set things up through a screen-share, even during a free trial! Does AWS or Azure do that? :)
"Everything you guys have been doing is amazing and being delivered as promised. As always you guys go above and beyond and I couldn’t be happier." - David Courville, Vice President of Information Technology - Definitive Healthcare

Customer Case Study
Enterprise cloud data management company improves control of application traffic and increases security and availability.
Read more
Schedule a No-Pitch Technical Demo
Want to learn more about how Web Application and API Protection (WAAP) might be able to solve your specific challenges?
Schedule a no-pitch technical demo with one of our engineers.
Demo Calendar