(without the need for hardware or software)
More than a dashboard, it's a multicloud application delivery controller.
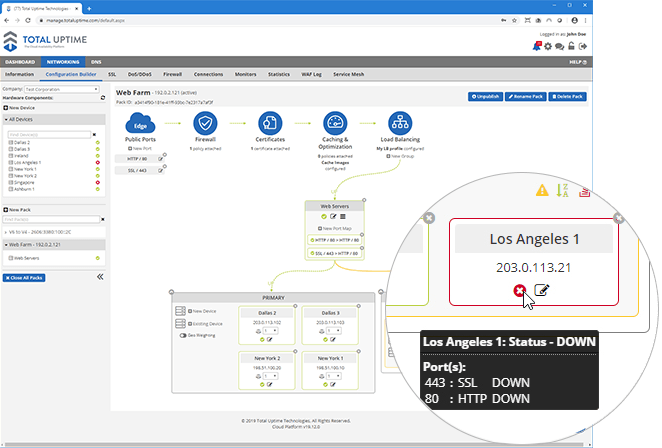
Send traffic to any device - anywhere!
World-class security for APIs, apps and devices
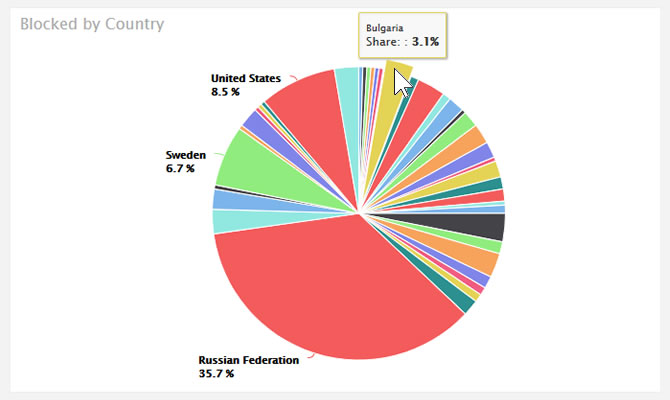
Ensuring everything remains connected is not a trivial task. With Total Uptime in the mix, managing multicloud or multi-site connectivity with numerous VPN tunnels becomes a lot easier, and with automation behind the scenes, ensuring availability is a breeze.
On-prem, hybrid-cloud, multicloud, it doesn't matter where your infrastructure resides with Total Uptime.
Multicloud Networking
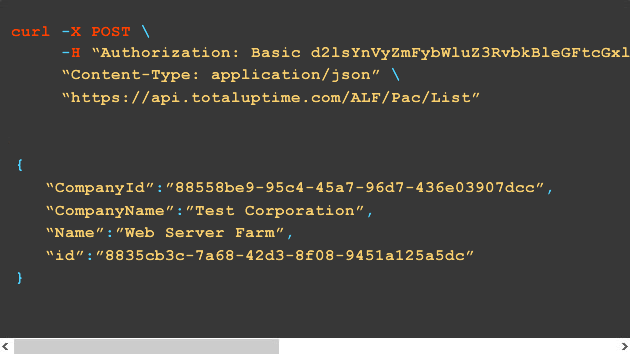
Total Uptime's REST API allows you to skip the UI, build your own, or simply automate and fit our features into your workflow. Our API offers in-depth documentation and how-to articles. Almost all of the data and functionality within our UI is accessible through the API, so the possibilities are endless.
Check our API Dox
When business applications are distributed around the globe using a multitude of disparate cloud platforms, ensuring availability, security and performance is incredibly difficult. Integrating those applications into an existing environment is also complex and introduces risk. Total Uptime gives our customers the tools to accomplish these things quickly and easily under one umbrella for total control.
We call this Enhanced Internet Delivery, or ADCaaS - Application Delivery as a Service.
Learn More About Us